Endpoint Detection & Response (EDR)
Know when an attacker is on your network
How do you stop an attacker in your environment when it’s not malware? Would you know if you had an active attacker on a machine in your network? Ascend helps you confidently answer these questions and defend against even the most advanced attacks.
77% of successful attacks last year utilized fileless attack techniques — something your traditional antivirus solution can’t detect or prevent. That’s why, when prevention fails, we have your back. Our Endpoint Detection & Response (EDR) service focuses on collecting and analyzing behavioral data to identify signs of an attack without relying on the presence of malicious files.

Detect the Unknown
Discover known & unknown
elements of an attack

Prevention Fails
Even the best security can’t provide 100% prevention

Know What Happened
Comprehensive attack timeline helps reduce investigation time
%
of attacks result in compromised network systems within MINUTES
%
of successful cyberattacks utilize fileless techniques
Protect your data and have greater visibility into advanced threats⏤all in a cost-effective manner.
the complete guide to Endpoint Detection
IT leaders play an important role in influencing and advising technology adoption in their organization — including the “growth stack” or set of tools designed to work together to achieve a strong security posture. With attacks becoming more advanced, bypassing the first lines of security protection, you need a security platform that pro-actively detects and stops threats before damage can be done.
You’re Protected Against:
(crimeware, ransomware, etc.)
Fileless
attacks
Misuse of
legitimate applications
Suspicious user
activity and behavior
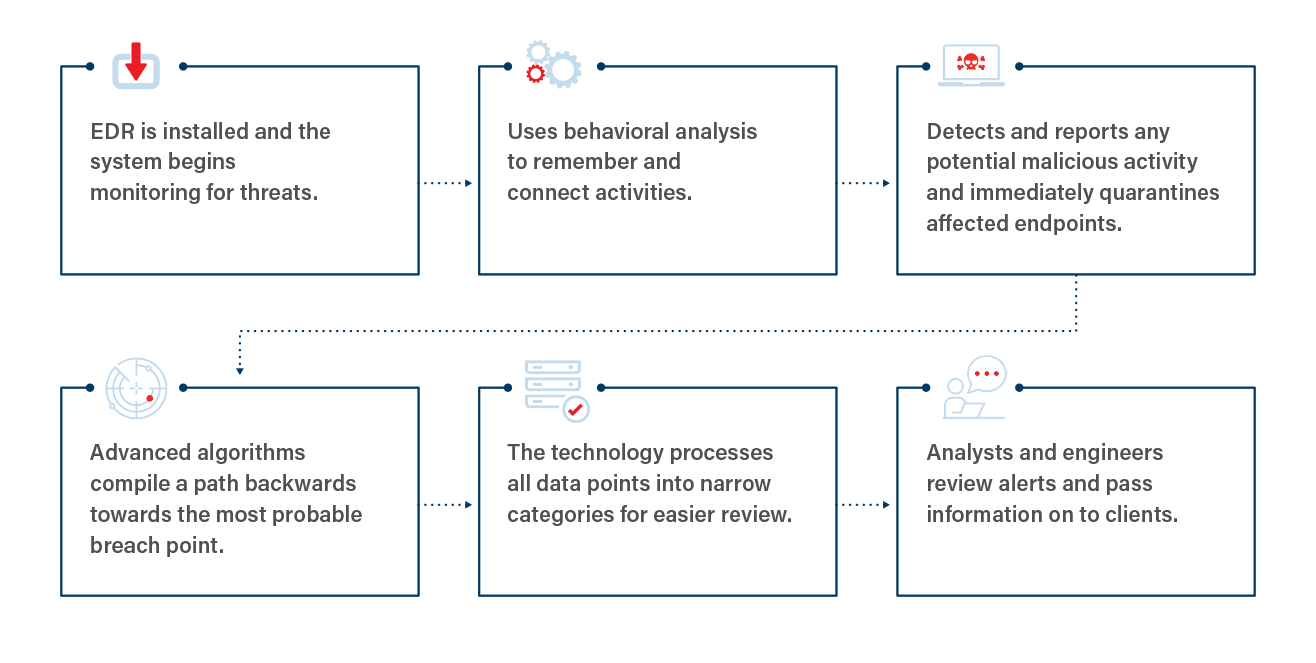
How Endpoint Detection & Response Works
EDR serves as a tripwire to alert and provide our 24×7 SOC with extensive information to find and detect the bad guy. Plus EDR stops attackers in their tracks before damage is done or data is exfiltrated.

Continue Exploring

eBook: The Complete Guide to Endpoint Detection & Response (EDR)
Datasheet: Endpoint Detection & Response (EDR)

Whitepaper: Small Business Firepower: A Case for Outsourced EDR




